Before we get into Horcruxing, here's a quick prologue on online security hygiene. You can skip to the Horcruxing section if it seems redundant.
Rules for Strong Online Security
1. Longer passwords (atleast 16 characters) are better than shorter ones
=> cutesamantha15101995 > cutesamantha
2. Randomized passwords are better than personally identifiable passwords
=> process-cancel-stingy-garnet > cutesamantha15101995
NOTE: process-cancel-stingy-garnet is technically a passphrase - basically an easy-to-remember password in comparison to randomized strings like B6fSpxMj&f6DU@5^k
3. Have a significantly different password for each account
Having the same password for different accounts is like using the same key for different locks. It beats the whole point of having multiple locks! Also, having different passwords but with only one easily guessable word different (like the ones below) still poses the same risk. The passwords should be significantly different.
bounce-unfold-stunning-chute process-cancel-stingy-facebook
symptom-untouched-unpaid-arena > process-cancel-stingy-twitter
sediment-tweak-annually-koala process-cancel-stingy-gmail
4. Use 2FA/MFA wherever possible
Both Google and Facebook offer a 2FA feature where you need the second factor only when you login from a new device or a new location, instead of needing 2FA every time. That's a rare combination of convenience & security right there! Most other sites also offer some variation of 2FA.
NOTE: Use the andOTP (or any other) app's TOTP as the second factor since it cannot be spoofed or spied on lock-screen like the SMS OTP and does not require a mobile network or internet connection. You can also use Biometrics (finger print or face recognition)
Woah! How do I create a long password for each of the bazillion websites out there, and have them significantly different and remember them? Security seems like such a pain in the ass!
[enter] PASSWORD MANAGER
A password manager helps you manage all your passwords in one place, either in the form of a browser extension, mobile app, or website. Good password managers will offer a browser extension and a mobile app with one-click auto-fill-login-page feature by removing the hassle of copy pasting or typing your login details. A few smart ones even detect phishing pages and warn you indirectly, by not showing the login details for such web pages.
They enable all the above measures for strong online security with ease. While I agree it takes some effort to set it up for the very first time. But, after that, it just flows like butter.
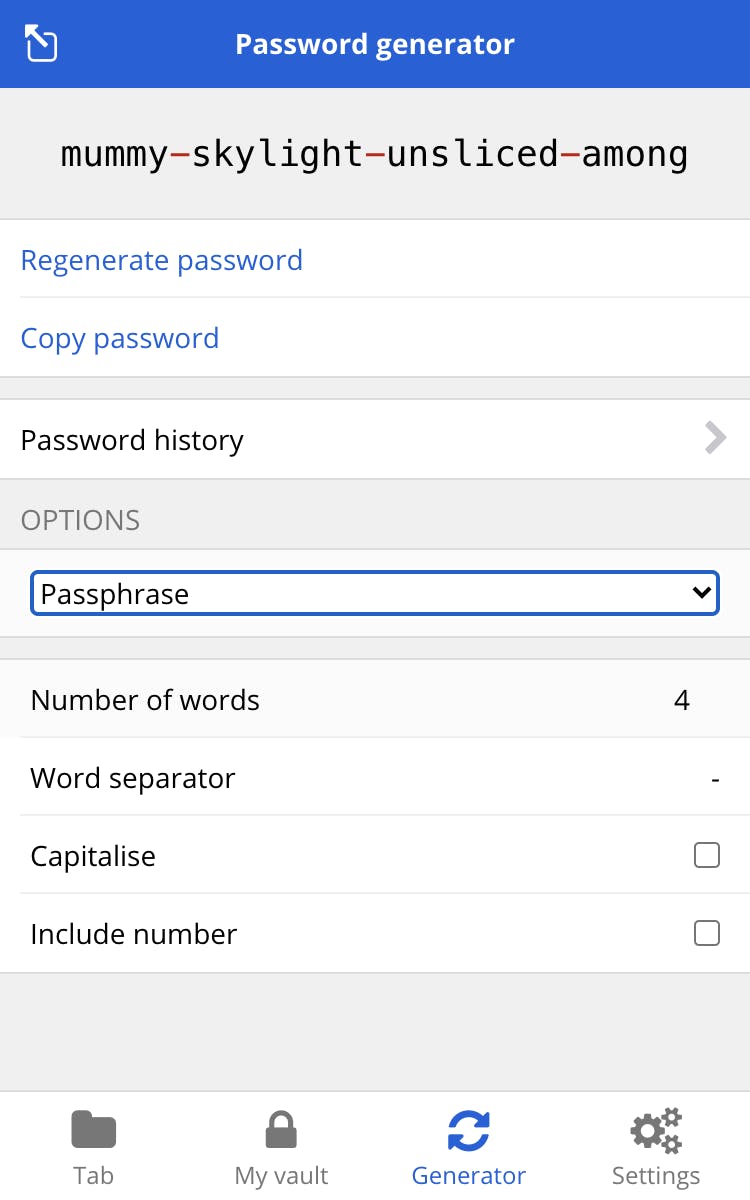
For example, password generator in BitWarden lets you custom design your random password in different flavours.
YAY! I'm Secure!
You meticulously move all your passwords and secrets to a trusted password manager. Finally, you can rest easy knowing that your digital life is truly secure. Or, is it?
- your master password (the password to your password manager) is compromised due to a security breach or you left it in plaintext on a post-it/ email/ notes app
- someone gained temporary access to your unlocked system (computer or phone) when you stepped away to get that last coffee for the day and your password manager is still logged in for everyone to see
The answer: you're screwed. The cost of putting all your eggs in one basket is that it could all go into oblivion in one fell swoop. How do you overcome this challenge now?
Double Blind Passwords (aka Horcruxing)
For all his faults, Voldemort did one good thing for us muggles. He gave us the concept of a horcrux. For the uninitiated, a horcrux is any object in which you store a piece of your soul, putting the proverbial eggs of your soul into different baskets, to gain quasi-immortality.
The basic idea: You split your password into 2 parts - one which is stored in the password manager, and the other which is stored in your head (aka horcrux).
Basically, at any given point in time, you and your password manager know only a piece of the password. It's double-blind. In effect, just like You-Know-Who, you're splitting your password (soul) into pieces and storing them in different places.
BEFORE
# As stored in the password manager
username: rick
password: rollthepeople1732
# Actual credentials
username: rick
password: rollthepeople1732
AFTER
# As stored in the password manager
username: rick
password: roll-the-people-venus
# As stored in your head
horcrux: papel
# Actual credentials
username: rick
password: roll-the-people-venuspapel
The horcrux adds an additional layer of security that only you can unlock. It's a kind of 2FA. Again, the longer the horcrux the better. But, a simple word should also be fine as long as only you know the horcrux.
If it feels like too much effort, use a horcrux only for the most important logins - your social media, bank accounts etc.
One Last Thing
Security is never absolute. One can try to secure a system as tightly as possible, but never really say that it is fully secure (if you see someone claiming otherwise, it's mostly marketing bullshit). If we cannot make systems completely secure, the next best thing to do is to make them as secure as possible and a good way to do it is Defense In Depth - basically make sure that even if one layer of security is breached, there exist other layers to mitigate further damage - which is what we've tried to achieve all along.
Summary
1. Use a good password manager
I use BitWarden (since it is open source and costs just $10 a year for the PRO features)
2. Use TOTP/ biometrics instead of SMS-based OTP
I use andOTP (since it is open source)
3. Use a horcrux (a double-blind password) for the most important logins
P.S. Keep in mind that horcruxing only works fine until you connect your brain to NeuraLink and accidentally upload your thoughts online for everyone to see. :P

